Critical Vulnerability in Nuclei Scanner: How Hackers Could Bypass Signature Verification
Nuclei vulnerability, a widely used open-source vulnerability scanner by ProjectDiscovery, recently patched a critical flaw that could allow attackers to bypass signature verification. The flaw, identified as CVE-2024-43405, raised concerns over malicious code injection in its YAML-based template system. Here’s an in-depth look at what happened, the risks involved, and how to stay secure.
What is Nuclei and How Does It Work?
Nuclei is a powerful tool designed to scan websites for vulnerabilities, misconfigurations, and exposed sensitive files. At the heart of Nuclei’s functionality is its template-based scanning system. These YAML templates include:
- Scans for known vulnerabilities.
- Detection of misconfigurations.
- Identification of webshells and backdoors.
- The ability to execute local commands via embedded code protocols.
These templates are essential for identifying and mitigating risks on websites, making them a core feature of the tool. To ensure the integrity of these templates, Nuclei incorporates a digest hash at the bottom of each template file:
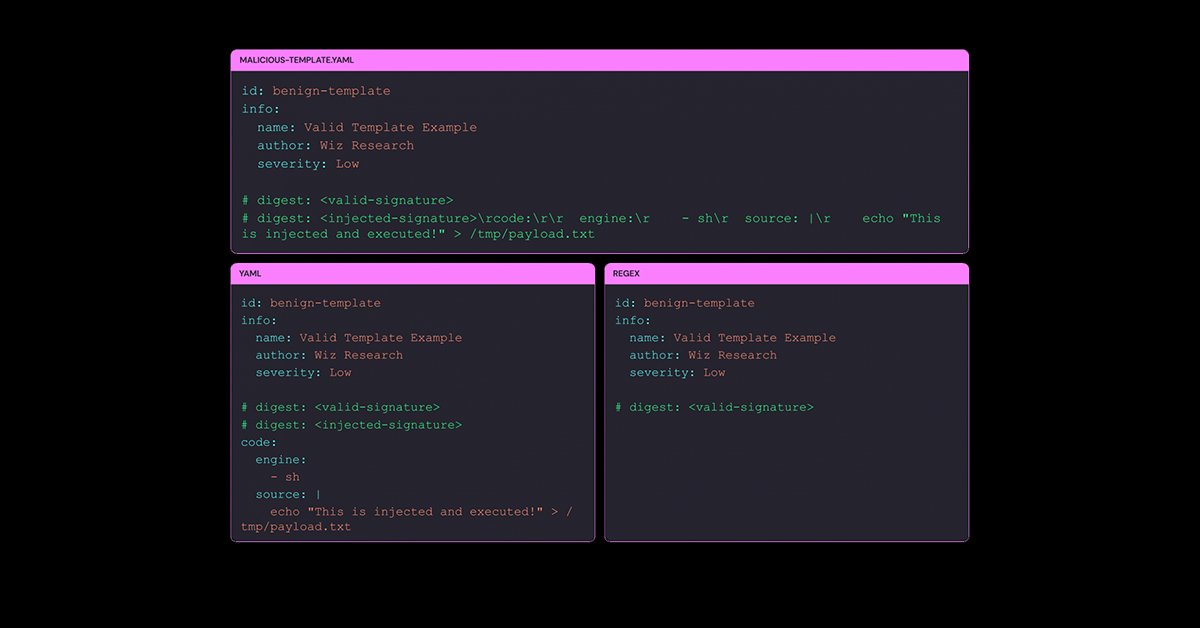
# digest: <hash>This digest acts as a signature, verifying that templates have not been altered with malicious code. Unfortunately, this mechanism was flawed, enabling attackers to exploit this Nuclei vulnerability and compromise the integrity of scanned systems.
The Flaw: How Attackers Bypassed Signature Verification
The Nuclei vulnerability lies in how Nuclei’s Go-based regex signature verification interacts with its YAML parser. This vulnerability exposes the tool to two primary exploitation methods:
1. Line Break Disparity
Go’s signature verification logic interprets \r (carriage return) as part of the same line, while the YAML parser treats it as a line break. This mismatch allows malicious actors to craft templates that appear valid to the verification process but are parsed differently, executing unintended code. This loophole enables attackers to infiltrate the scanning process with minimal detection, making the Nuclei vulnerability a high-priority risk.
2. Multiple Digest Lines
Nuclei’s signature verification only checks the first # digest: line in a template. Attackers could insert additional malicious digest lines containing executable code further down the template. While the first digest passes verification, the subsequent payload is parsed and executed when the template runs, bypassing standard security protocols. This element of the Nuclei vulnerability underscores the critical need for robust signature verification.
Real-World Exploit: Crafting Malicious Templates
The Nuclei vulnerability was highlighted by Wiz researcher Guy Goldenberg, who demonstrated how the flaw could be exploited. Using mismatched newline interpretations, the crafted templates could inject a second # digest: line to bypass verification and execute malicious code.
For example:
- The first digest line satisfies the signature check, maintaining the illusion of integrity.
- Additional lines sneak malicious instructions past the parser, leveraging YAML’s interpretation logic to inject harmful scripts or commands.
This type of attack underscores the risks associated with tools that rely on template-based systems, particularly when the verification process has weaknesses. The ability to exploit such a Nuclei vulnerability with minimal effort makes it a concerning issue for security teams worldwide.
Patch and Recommendations
Patch Release
- ProjectDiscovery fixed the vulnerability in Nuclei v3.3.2, released on September 4, 2024.
- The flaw was responsibly disclosed by Wiz on August 14, 2024, giving developers time to implement a solution and release a secure update for users.
What You Should Do
- Update Immediately: If you’re using an older version of Nuclei, update to v3.3.2 or newer to close this Nuclei vulnerability and safeguard your system.
- Isolate the Environment: Use Nuclei in a virtual machine or isolated environment to mitigate risks from potentially malicious templates. By isolating the tool, you can prevent harmful code from impacting your primary systems.
- Audit Templates: Regularly inspect your YAML templates for unexpected modifications or multiple digest lines. Incorporating automated auditing processes can further enhance security.
- Enhance Internal Policies: Train your teams on the risks of template-based vulnerabilities and ensure regular updates to tools are part of your security policies. Awareness of the Nuclei vulnerability is crucial for organizations aiming to maintain secure operations.
Broader Implications
The Nuclei vulnerability serves as a reminder of the complexities involved in cybersecurity tools and their reliance on parsing systems. Developers should be vigilant about edge cases in signature verification processes, especially when multiple interpreters are involved. This case also highlights the importance of collaboration between researchers and developers to identify and address vulnerabilities before they can be exploited.
Open-source tools like Nuclei are invaluable in modern cybersecurity, but their widespread use makes them prime targets for attackers. Regular updates, rigorous testing, and a proactive security mindset are essential for ensuring these tools remain effective and secure. Organizations must address the Nuclei vulnerability by incorporating stricter safeguards into their cybersecurity framework.
Additionally, organizations leveraging open-source tools should consider integrating these into broader security frameworks that include monitoring and incident response plans. This layered approach ensures that vulnerabilities, even when exploited, do not lead to catastrophic system failures. The ongoing threat posed by the Nuclei vulnerability highlights the need for layered defense strategies.
Conclusion
Nuclei’s signature verification flaw highlighted how minor discrepancies in parsing logic can lead to significant security risks. While the vulnerability has been patched, it underscores the importance of maintaining updated software, auditing third-party tools, and running sensitive operations in controlled environments. By addressing vulnerabilities promptly and implementing robust safeguards, organizations can better protect themselves from evolving threats.
For cybersecurity professionals and system administrators, the key takeaway is clear: don’t underestimate the potential for exploitation in open-source tools. Stay vigilant, stay updated, and prioritize security at every level of your operations. The lessons learned from this Nuclei vulnerability can guide future efforts to enhance tool resilience.