- Banshee Stealer Malware: The MacOS Malware That “Borrowed” from Apple’s XProtect
- Why macOS Users Are Becoming Prime Targets
- <strong>Banshee Stealer Malware</strong>’s Evolution and Stealth Techniques
- Method of Distribution: Phishing Websites and GitHub Repositories
- Core Capabilities: Credentials, Wallets, and More
- Dark Web Activities & The Source Code Leak
- Mitigation Strategies: Staying One Step Ahead
- Conclusion
Banshee Stealer Malware: The MacOS Malware That “Borrowed” from Apple’s XProtect
MacOS users often hold a persistent belief that Apple’s operating system is inherently safe from malware. However, recent developments with Banshee Stealer Malware reveal that cybercriminals are actively exploiting vulnerabilities in MacOS, leveraging encryption techniques originally introduced by Apple’s XProtect antivirus engine. Despite Apple’s built-in security tools like Gatekeeper, XProtect, and system sandboxing, the evolving nature of stealthy macOS stealers should make even the most casual users think twice about their safety.
In this article, we’ll explore how Banshee Stealer Malware evolved into a formidable stealer-as-a-service threat, delve into its distribution channels, and discuss proactive steps to mitigate this growing menace.
Why macOS Users Are Becoming Prime Targets
The global macOS user base has surpassed 100 million, marking roughly 15.1% of the total PC market share. This expanding footprint has shifted attacker attention from traditional Windows-focused payloads to Mac-based strategies. Cybercriminal forums on the dark web are buzzing with advertisements for new MacOS-focused exploits. The rise of Banshee Stealer Malware exemplifies how advanced threats are adapting, specifically aiming at cryptocurrency wallets, browser credentials, and system files stored on unsuspecting machines.
The False Sense of Security
Historically, MacOS benefited from “security through obscurity,” being overshadowed by the sheer volume of Windows users. However, with Apple’s market share on the rise, more malicious actors see macOS as a profitable playground. Many users continue to undervalue the need for antivirus solutions or cybersecurity awareness training, giving threats like Banshee a golden opportunity to thrive.
Banshee Stealer Malware’s Evolution and Stealth Techniques
Stolen Encryption From XProtect
Initially discovered by Check Point Research, Banshee drew attention for “borrowing” its string encryption algorithm from Apple’s XProtect. This approach helped the malware evade detection, as many antivirus engines failed to recognize the malicious patterns hidden behind a method that mirrors Apple’s legitimate security practices. The result? A two-month window where Banshee went largely undetected on VirusTotal and other scanning platforms.
Anti-Analysis and Child Processes
Beyond encryption, Banshee Stealer Malware employs intricate anti-analysis tactics. It uses the Unix fork() function to spawn a child process, thwarting attached debuggers. Before terminating the parent process, it executes killall Terminal, closing any active Terminal sessions. The child process then calls setsid(), which starts a background daemon that blends into normal system tasks. This multi-layered approach effectively disguises malicious operations, making Banshee even harder for investigators to trace.
Persistence and Silence
If the malware acquires root directory write-and-execute permissions, it redirects stdin, stdout, and stderr to /dev/null, allowing it to run “silently” in the background. This “no-output” condition prevents suspicious logs from appearing, further complicating detection for security analysts.
Method of Distribution: Phishing Websites and GitHub Repositories
Threat actors employ a multi-faceted distribution strategy, using:
- Phishing Websites – Fake pages impersonating popular software like Telegram or TradingView trick macOS users into downloading infected
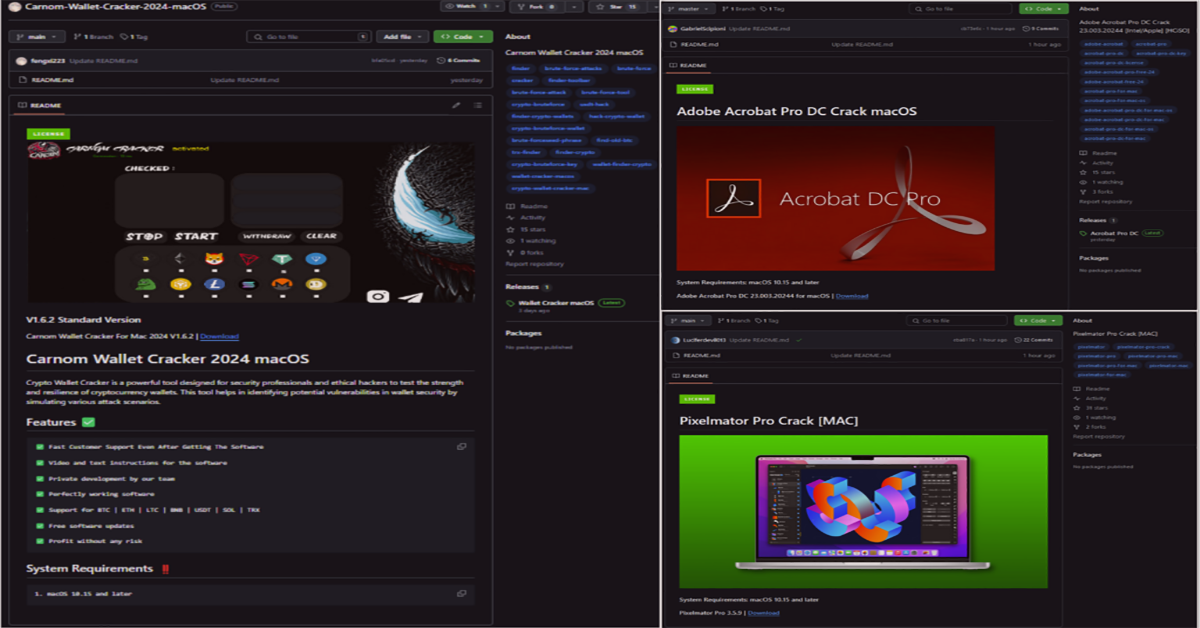
.dmgfiles. - Malicious GitHub Repositories – Posing as cracked or pirated software (e.g., Adobe tools), attackers upload stealthy versions of Banshee for macOS, as well as Lumma Stealer for Windows users.
Notably, some repositories exhibit suspiciously high “stars” and “commits,” giving them a false sense of legitimacy. Attackers then update the readme to include direct download links or redirect victims to GitHub.io pages that offer malicious .zip or .dmg files. Such tactics enable cross-platform infections, hitting both Windows and MacOS.
Core Capabilities: Credentials, Wallets, and More
Browser Credential Theft
Banshee Stealer Malware targets popular browsers including Chrome, Brave, Edge, Vivaldi, Yandex, and Opera. By decrypting stored usernames and passwords, this macOS infostealer obtains immediate access to a victim’s online accounts.
Cryptocurrency Wallets in the Crosshairs
Cryptocurrency has long been a magnet for cybercriminals. Banshee Stealer Malware methodically harvests data from browser extensions linked to wallets like MetaMask, Coinbase Wallet, Phantom, Keplr, and many more. It also scans for wallet software, such as Exodus, Electrum, Guarda, Wasabi, and Ledger. Once stolen, these digital assets can be rapidly exfiltrated to the attacker’s accounts, causing irreversible financial losses.
MacOS Password Prompt Scam
To bolster its data collection, Banshee displays a pop-up mimicking legitimate system updates, tricking users into entering their macOS password. It validates the password via dscl /Local/Default -authonly, storing the credentials for future misuse.
File Grabber and System Profiler
Leveraging AppleScript, Banshee Stealer Malware rummages through Desktop and Documents folders, selectively exfiltrating files under 50KB with extensions like .txt, .doc, .wallet, or .key. It also runs system_profiler SPSoftwareDataType SPHardwareDataType to compile OS and hardware details. Finally, the malware zips, XOR-encrypts, and Base64-encodes the stolen data, sending it via a POST request to its Command and Control (C2) server.
Dark Web Activities & The Source Code Leak
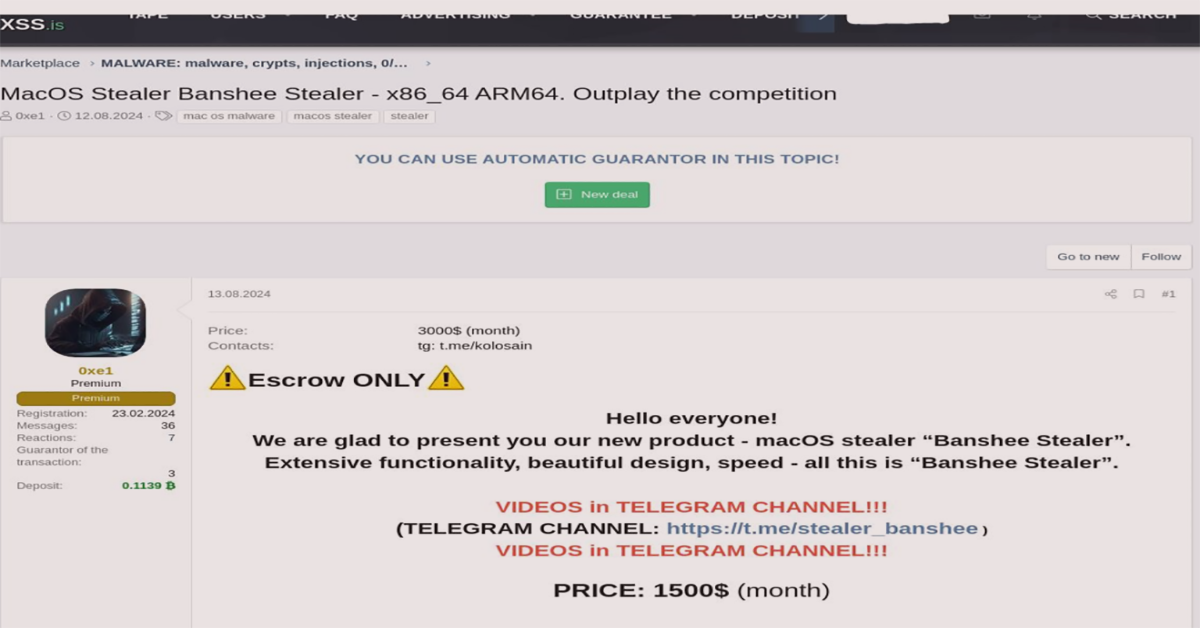
Banshee Stealer Malware initially sold for $2,999 on Telegram, but soon after, the author promoted it on prominent cybercriminal forums like XSS and Exploit. By August, the operator offered a private group service model, seeking affiliates for high-profit campaigns targeting macOS users.
However, on November 23, 2024, the original Banshee source code leaked on the XSS forums. Within 24 hours, the author shut down public operations. Despite this, Check Point Research still observes new Banshee Stealer Malware campaigns. It’s unclear whether the same operator or other malicious groups—now armed with the leaked code—continue to launch phishing campaigns. After the leak, antivirus engines, which had struggled to detect Banshee’s encrypted strings, updated their rules. Yet, the risk remains that multiple “forked” versions of Banshee could emerge, each employing variations of the leaked code to stay one step ahead of detection.
Mitigation Strategies: Staying One Step Ahead
- Keep Software Updated
Regularly update macOS, browsers, and antivirus programs to patch vulnerabilities. Apple frequently rolls out security updates that address newly discovered threats. - Exercise Caution with Downloads
Avoid downloading “cracked” software from GitHub or unknown phishing websites. Check user reviews, star counts, and commit histories, but be aware that these can be manipulated. - Use Strong Antivirus Solutions
Opt for reputable third-party antivirus or anti-malware tools. Modern solutions often include behavioral analysis capable of detecting suspicious processes like Banshee’s stealthy forks. - Enable Multi-Factor Authentication (MFA)
Even if Banshee steals your browser credentials, having MFA will add a second layer of defense against unauthorized logins. - Train Employees and Home Users
Human error is often the weakest link. Provide or seek out regular cybersecurity awareness training to help identify phishing red flags, suspicious GitHub repositories, and fraudulent pop-ups.
For more advanced defense techniques, see our Endpoint Security Best Practices. You can also explore Apple’s official macOS Security and Privacy documentation for deeper insights on native safeguards.
Conclusion
The rise of Banshee Stealer Malware underscores the growing tide of macOS-focused malware, highlighting the urgency for robust security practices. By employing Apple’s own encryption method, Banshee managed to evade most detection solutions for months, exfiltrating credentials and siphoning cryptocurrency with startling efficiency. Although the operation reportedly “closed” following the source code leak, threat actors are still repackaging this malicious code, distributing it through phishing websites and malicious GitHub repositories.
Staying protected is a proactive endeavor. Keep your devices updated, exercise caution when downloading software, and adopt multi-factor authentication whenever possible. With macOS no longer immune from sophisticated threats, vigilance is key to ensuring your data remains safe.
Summary
Banshee Stealer Malware is a stealthy macOS malware that leverages Apple’s own XProtect encryption methods to remain undetected. Disguised as cracked software or delivered through phishing pages, it specifically targets browser credentials, cryptocurrency wallets, and sensitive user data, making it a significant threat to macOS users. After its source code leaked on underground forums, antivirus programs began detecting Banshee more reliably. Nonetheless, multiple variants continue circulating, emphasizing the need for consistent security updates, phishing awareness, and multi-factor authentication. By staying informed and following basic cybersecurity best practices, users can mitigate the risks posed by Banshee Stealer Malware and other emerging threats.