BadRAM Attack: Unveiling Vulnerabilities in AMD Processors
Recent research by European universities has shed light on the BadRAM attack, a unique method of exploiting vulnerabilities in AMD EPYC processors by manipulating RAM modules. This sophisticated attack primarily threatens cloud solution providers and virtualization systems, exposing the encrypted data of highly secure virtual machines. This article explores the details of this emerging threat, explains the underlying technology, and provides actionable strategies to mitigate potential risks.
Understanding Trusted Execution Environments (TEE)
Trusted Execution Environments (TEEs) are designed to isolate sensitive data and processes from the rest of a system’s code. With software errors being inevitable—an estimated 1 to 20 per 1,000 lines of code—TEE offers a protective layer against vulnerabilities that malicious actors can exploit. By isolating critical operations, TEEs help safeguard processes like private encryption key handling or financial transaction verifications.
For instance, TEEs such as AMD’s Secure Encrypted Virtualization (SEV) encrypt virtual system data, ensuring that neither other virtual systems nor physical server operators can access it. SEV’s introduction has enhanced the protection of virtualized environments by reducing the risk of unauthorized access to sensitive information.
Features of Secure Encrypted Virtualization
- Data Encryption: SEV encrypts virtual machine (VM) data in memory, ensuring isolation from other systems and preventing unauthorized access.
- Unauthorized Access Detection: The Secure Nested Paging extension detects unauthorized attempts to access VM data, adding an additional layer of protection.
- Independent Operation: SEV operates using a separate processor module within the server, further isolating it from main processor cores and minimizing cross-application vulnerabilities.
Despite these robust features, the BadRAM attack demonstrates that even the most secure environments can be compromised under specific conditions. The attack’s implications highlight the need for continuous innovation in TEE development.
The Mechanics of the BadRAM Attack
The BadRAM attack exploits the trust that processors place in RAM module specifications. Attackers leverage this trust to bypass SEV’s encryption and Secure Nested Paging mechanisms. Here’s how it works:
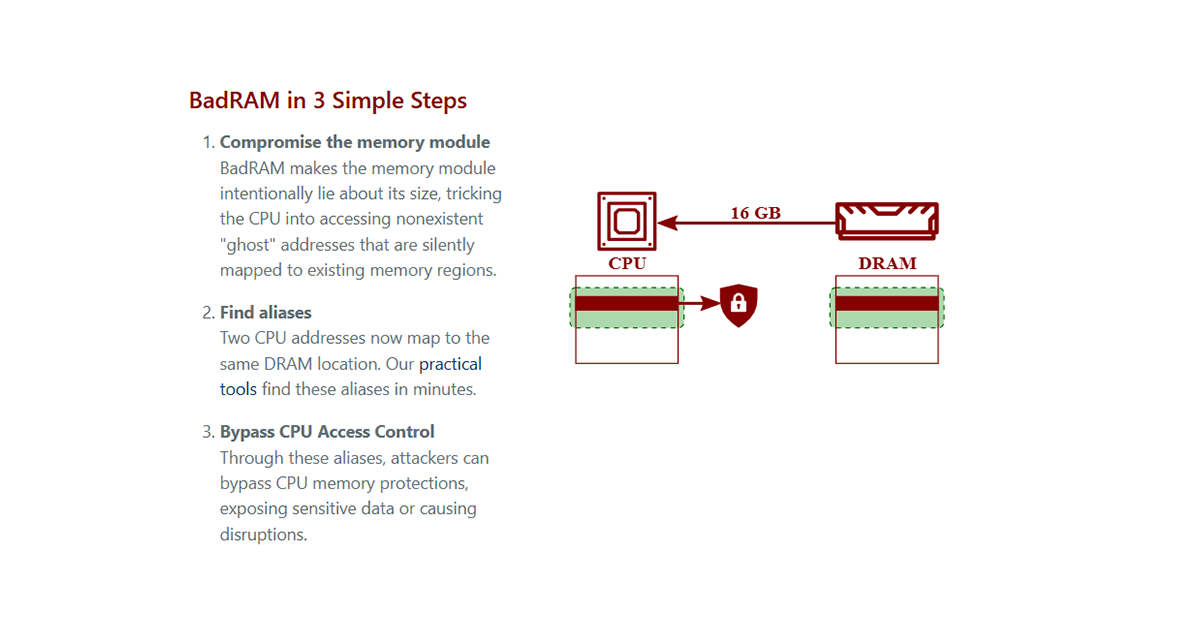
- RAM Modification: Attackers reprogram the SPD (Serial Presence Detect) chip of a 32GB RAM module to falsely report its capacity as 64GB.
- Processor Deception: The processor, relying on the modified SPD data, attempts to utilize the RAM as though it has twice its actual capacity.
- Dual Mapping of Memory Cells: This misreporting causes real memory areas to be shared between a protected virtual OS and a malicious application, enabling the latter to read encrypted data.
This attack effectively creates a loophole where secure data becomes accessible to unauthorized entities. By manipulating the SPD chip, attackers achieve a level of access that was previously considered improbable without expensive hardware or physical intrusion.
Broader Implications and Challenges
The attack bypasses SEV’s encryption protocols, making the encrypted data of virtual systems vulnerable. While the attack requires physical access and significant privileges to execute initially, subsequent stages can often be carried out remotely. This has several implications:
- Lower Barrier to Entry: Compared to earlier methods, the BadRAM attack is much more affordable. Using a $10 microcomputer and software kit to modify the SPD chip significantly lowers the cost and complexity of the attack.
- Wider Attack Surface: The exploitation method raises concerns about other potential vulnerabilities in memory modules and their interactions with processors.
- Cloud Security Concerns: Cloud service providers, which rely heavily on virtualization technologies, are particularly at risk if proper countermeasures are not implemented.
For comparison, previous studies achieved similar results using a $170,000 hardware device to intercept data in real-time. The BadRAM attack’s relative simplicity and affordability underscore its disruptive potential.
Mitigation and Prevention
Fortunately, AMD has addressed these vulnerabilities in its EPYC 3rd Gen and 4th Gen processors through firmware updates. These updates introduce mechanisms to detect malicious memory modules. Additionally, Intel’s Trusted Domain Extensions (TDX) already feature RAM integrity checks, which mitigate similar risks.
Key Recommendations for Organizations
- Firmware Updates: Ensure that all servers using AMD EPYC processors are updated with the latest firmware. Regular updates are critical to maintaining system security.
- Physical Security: Restrict physical access to servers and critical hardware to prevent unauthorized tampering.
- System Monitoring: Implement advanced monitoring solutions to detect and respond to unauthorized changes in system configurations in real-time.
- Vendor Audits: Evaluate the security measures of cloud and hosting providers, ensuring adherence to best practices in TEE implementation.
- Education and Training: Train IT staff on emerging threats like BadRAM attack to enhance organizational readiness.
The Bigger Picture: TEE Limitations and Future Directions
The BadRAM attack underscores the limitations of current TEE implementations, even in highly secure environments. Developers often assume that extracting data from RAM is sufficiently challenging to deter attackers. However, this study highlights how even relatively simple techniques can bypass sophisticated security measures.
Key Takeaways
- Complexity vs. Vulnerability: The increasing complexity of TEEs does not guarantee immunity to attacks. Security mechanisms must evolve to counter new exploitation methods.
- Proactive Defense: Organizations must adopt proactive strategies, such as routine security assessments and continuous monitoring, to stay ahead of emerging threats.
- Collaboration: Ongoing collaboration between researchers, hardware manufacturers, and industry players is essential to identify and address vulnerabilities promptly.
- Broader Implications: The findings emphasize the need for a shift in security paradigms, focusing on addressing vulnerabilities at both hardware and software levels.
Conclusion: Navigating the Threat Landscape
The BadRAM attack serves as a wake-up call for the cybersecurity community. While it is a highly complex attack requiring significant expertise and resources, it highlights the vulnerabilities inherent even in advanced technologies like SEV. By staying informed, adopting best practices, and investing in robust security measures, organizations can fortify their defenses against such sophisticated threats.
Cybersecurity is an ever-evolving field, and threats like BadRAM attack demonstrate the critical importance of vigilance and adaptability. For cloud providers, businesses, and IT professionals, this means maintaining a proactive stance and collaborating to secure the technology landscape.