A critical vulnerability has been uncovered in Telegram, posing a significant threat of session hijacking through XSS (Cross-Site Scripting). This vulnerability affects versions of Telegram WebK prior to 2.0.0 and extends its impact to web3 users. Despite awaiting a CVE assignment, Telegram has taken rapid action to patch this vulnerability, ensuring user security.
Technical Analysis
Telegram’s unique feature, Telegram Mini Apps, enables web applications to operate seamlessly within the Telegram Messenger Interface. While enhancing user experience with features like seamless authorization and integrated payments, this feature inadvertently created an avenue for exploitation. Malicious Mini Web Apps could execute arbitrary JavaScript under the guise of web.telegram.org, potentially compromising any Telegram user’s session.
The XSS vulnerability is triggered through the web_app_open_link event type via post message. By exploiting this event type, threat actors could manipulate URLs to save exploited content within the JavaScript of web.telegram.org while opening a new URL tab.
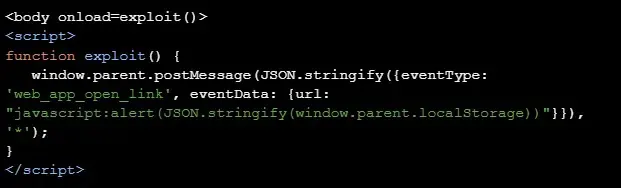
Patch Implementation
Telegram responded promptly by implementing a patch that includes a safeWindow URL and adds the noreferrer argument to tab openings. This measure isolates the new window from the original Telegram window, mitigating risks associated with JavaScript execution. Users are strongly advised to upgrade to Telegram WebK 2.0.0 (488) to prevent exploitation of this vulnerability.
By addressing this vulnerability swiftly, Telegram demonstrates its commitment to user security. It’s imperative for users to prioritize security by staying informed and promptly applying updates to mitigate potential risks. Protect your Telegram session today by upgrading to the latest version.






